All About Cybersecurity
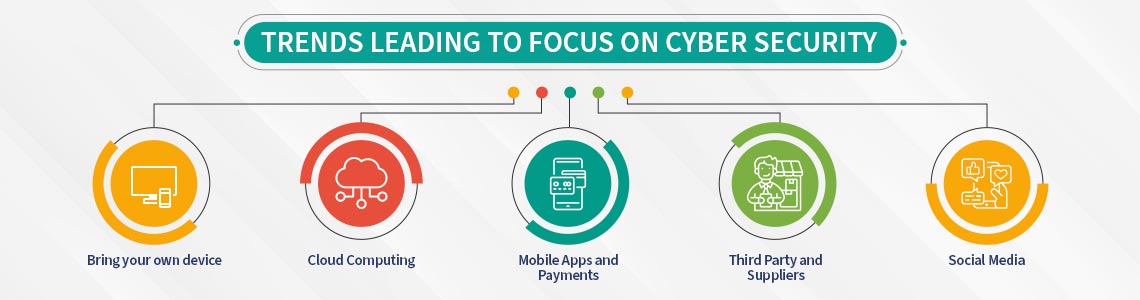
Adoption of AI, ML, Internet of Things (IoT), and other digital technologies has brought about an increasing volume of data, putting data privacy and security at constant risk of cyber attacks.
Organisations need to be constantly alert to cyberthreats by cybercriminals, who are always on the lookout for stealing critical data of organsiations, their clients and employees. Also at risk is citizen data from government records, which is then sold for financial gains.
A cumulative revenue of USD 4.3 Bn was generated by the industry in 2019, with major revenue coming from system integrators, working on planning, coordinating, implementing, improving, even maintaining the computing operations for their clients. The industry is estimated to register an overall CAGR of 21% by 2025.
Market Growth & Opportunities
Today, more than 50-55% companies are working on a platform/IP as a part of their future strategy. Thereby establishing a space for cybersecurity companies to create effective solutions in collaboration with such organisations. The employee base of the cybersecurity services companies is anticipated to scale up largely from the current 1,10,000 in the foreseeable future. It is noteworthy that more than 35% companies are re-skilling/upskilling their security workforce.
Threats
Today, the need for cybersecurity has become urgent with people forced to work remotely, putting themselves at the mercy of cyberattacks due to lack of proper cyber protection. Some of the threats faced in 2020 included phishing, ransomware, cryptomining, IoT and state-sponsored attacks, data leakage, insider threats, cyber-physical attacks and more.
Solutions
In the coming year we should see cybersecurity measures being taken across all digital platforms; also in governance, especially for crowdfunding, open banking and auditing purposes; for protection of intellectual property, microgrids, stock trading and even 5G.
Global Key Trends
Security ecosystem
The five broad categories are:
- Perimeter, Network and Host Security
- Application and Endpoint Security
- Data Security
- GRC & Audit
- Security Orchestration
Perimeter, Network and Host Security is like building a strong wall around your premises with routers and firewalls to prevent any outside attacks and control access to your networks. Network and Host Security is the capability of taking hardware and software precautionary measures via a user interface to protect the network infrastructure and host, like the security at your entrance.
- Firewall is the first line of defence in a network security system that controls incoming and outgoing traffic.
- NGFW or Next-Gen Firewall is an inspection firewall that adds application-level inspection and intrusion prevention. It is a part of the third generation of firewall technology.
- Intrusion Detection System (IDS) monitors network traffic for malicious activity or policy violations. It sends out alerts if any suspicious activity or violation is found.
- Intrusion Prevention System (IPS) has the ability to respond to detected intrusions, preventing identified threats.
- Vulnerability Assessment (VAS) is a process that scans computers, communications infrastructure and network security systems, identifying and preventing security gaps and vulnerabilities.
- Anti-Virus software is a set of programs that detect and remove software viruses, and other malicious software like worms, trojans, adware, and more.
- Malware Detection is a malicious software, developed to infiltrate, disrupt and damage a computer or mobile system. It is used to detect the presence of malware (a malicious s/w) on a host system.
Application and End point Security safeguards data and workflow for identifying gaps or vulnerabilities in cybersecurity policies of applications or underlying packages.
- End Point Detection and Response (EDR) safeguards, detects, investigates, and blocks suspicious applications and issues on hosts and endpoints, preventing data loss.
- SSL Certificate Managern allows secure network communications and identify websites and resources on private networks.
- Web Application Firewall (WAF) is an application firewall for HTTP applications. It applies a set of rules to an HTTP conversation that generally cover common attacks such as cross-site scripting (XSS) and SQL injection.
- Penetration Testing (PenTest) is a security exercise for a computer system, network or web applications to protect exploitable vulnerabilities.
- Web Gateway or Application Vulnerability Scan (AVS) is used for standardisation to compare applicants accurately. It looks for security vulnerabilities such as Cross-site scripting, SQL Injection, Command Injection, Path Traversal and insecure server configurations.
Data Security is critical for today’s businesses. It means protecting data from destructive forces and unauthorized users.
- Identity as a Service (IDaaS) provides cloud-based authentication and access control for identity management in organisations for their growing number of single-use sign-on.
- File Integrity Management (FIM) detects changes in files and validates the integrity of the operating system and application software files. Thus preventing cyberattacks.
- DB Vulnerability or Activity Monitoring are automated tools that scan Vulnerabilities in Database such as SQL Server, Oracle, MySQL etc.
GRC and Audit allows public companies to integrate and manage IT operations within the gambit of their regulations.
- Security Audit protects companies from security risks. It is a technical assessment of a system or application.
Security Orchestration regulates and automates security solutions of different systems, ensuring they work well together.
Job Roles
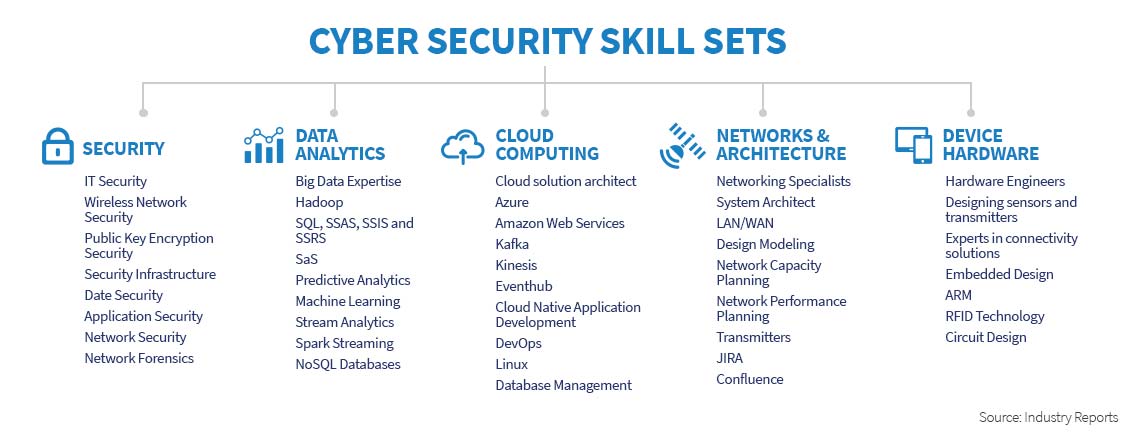
With the rapid pace of digitization, the demand for cybersecurity professionals is among the highest. By upskilling in the technology, professionals can progress as Analysts- for Application Security, Identity and Access Management, End Point Security, and Operations Centre Security. Explore career opportunities as a Penetration Tester, Network Security Consultant, Forensic Specialist, and Security Infrastructure Specialist.
FutureSkills Prime offers an industry-aligned portfolio of learning solutions. Every program is validated by SSC nasscom and backed by certification from the Government of India. This means learners can be sure that every program that is made available is industry-relevant and in this case, one of the best cybersecurity certification for beginners and higher training programs.


